Do you usually notice break-glass boxes in trains, buses, or buildings? Hopefully, you haven’t had to use them, but they are a comforting safety measure. Did you know that, similarly, Azure Active Directory enables you to create a break glass account in case of an emergency? For example, imagine a situation where you’ve lost or don’t have access to all your devices with Multi-Factor Authentication, or you can’t reach any of your admins. Still, you desperately need to log in to your Azure AD as quickly as possible. No worries, your break-glass account will help you!
In this article, you will learn about break glass accounts, when they should be used, and vital information for setting up and monitoring them in Azure Active Directory.
What is a Break Glass Account?
A break glass solution is a non-personal account that should only be used in case of an emergency. This high-privilege information is stored in a secure place, meaning only a few people in your organization can access it. Standing in as the Global Admin of your Azure AD, it provides the help needed only when access to other accounts or measures can’t be used.
When do I use the Break Glass Account?
You only use a break glass account in high-risk situations, when all the other regular admin accounts (like On-Prem Active directory) are compromised or cannot be reached. Some examples are:
- If your ADFS environment is down and your employees cannot log in anymore. This account can help you move the domain from federated to managed, so work can continue while your ADFS environment is getting fixed.
- When Azure Multi-factor authentication service is down, or the devices using this service are no longer available, you can temporarily disable your conditional access features.
- There is an issue accessing your environment. There are many reasons for this including – the regulations around your Azure AD Conditional Access policy, no administrators can help you at the time, or the policy admin has left your organization.
- Any unforeseen natural disaster that can’t be predicted.
Since this account is extremely privileged, access data should be stored in a secure place. Think of it as a lock safe, and is only used when no other resources are available. This account doesn’t have conditional access policies (ex: two-factor authentication), so it can be easily accessible with correct login data.
Something to be aware of with this account is password time durations. This limitation aims to control and reduce the account’s usage to only when necessary. If you use your break glass account once, similar to breaking the glass to trigger a fire in your building, the account must be restored in a timely manner, ready to assist in the next emergency.
How do I set up a Break Glass Account?
It is important to set up your account correctly. Follow these three steps to get your back-up plan up and running:
- Create a User Option
- Monitor Sign-Ins and Audit Logs
- Create an Action Group
1. Create a User Option
The first step is choosing the Create User option, as shown in the picture below.
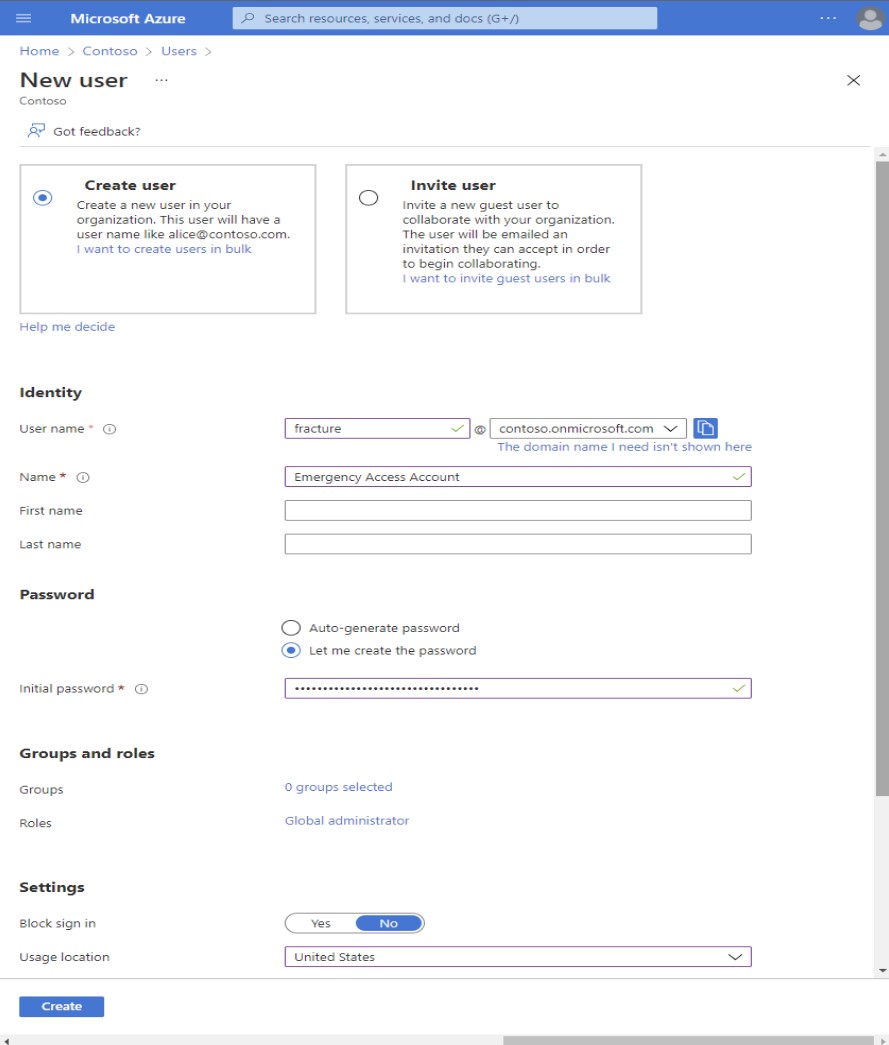
The identity portion of setting up the account is like any other registration. You need to make sure you use @.onmicrosoft.com as the Username. Then you need to name your account. We suggest you use something recognizable, like Emergency Access Account or a break glass account, so you can easily distinguish this account from the others in Azure AD. After filling in those fields, type your first and last name.
This account should have a strong password, with at least 16 characters and as complex as possible (with both capital and small letters, numbers, and special characters). We strongly suggest using our option to generate a strong password and store it in a safe place. A hard-to-guess, complex password protects your account from unauthorized access or hacking. In addition, you should assign the GlobalAdmin role to your account, so it has all privileges needed to help you in emergencies.
Your account should be top secret and excluded from all built-in access control policies, since you will be the one using the account in exceptional cases. Your break glass account should be excluded from all the following services:
- Azure AD conditional access policy.
- Azure MFA
- SSPR
- Azure Identity protection
2. Monitor Sign-In and Audit Logs
Break glass accounts should only be used for testing and actual emergencies. Monitoring these accounts is an excellent practice for organizations, so emergencies or undesired actions can be detected immediately. By frequently checking the sign-in and audit logs, you can detect all the activity on this account.
Azure Log Analytics is a great tool for monitoring your emergency accounts, allowing you to be notified via SMS and email alerts whenever there is an activity on the account. The picture below shows how monitoring is performed and how logs from the detected activity are created.
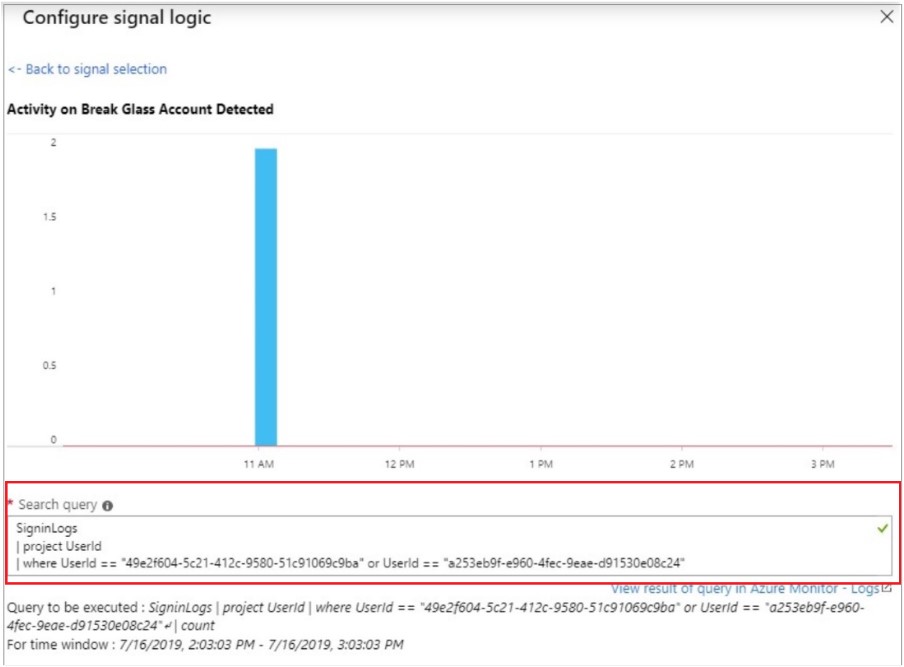
Since each login to the break glass account is being monitored, alerts should be based on the number of results greater than 0, as presented in the photo below. After setting up that logic, you can choose the frequency of the check evaluation. We suggest generating 5 assessments every 5 minutes to ensure top notch security.

3. Create an Action Group
For monitoring sign-in and audit log activities, you should add an action group to receive the alerts, like in the picture below. The group is created by assigning a name and short name, choosing the type of subscription they have within the environment, and choosing Default-ActivityLogAlerts as a resource for this group.
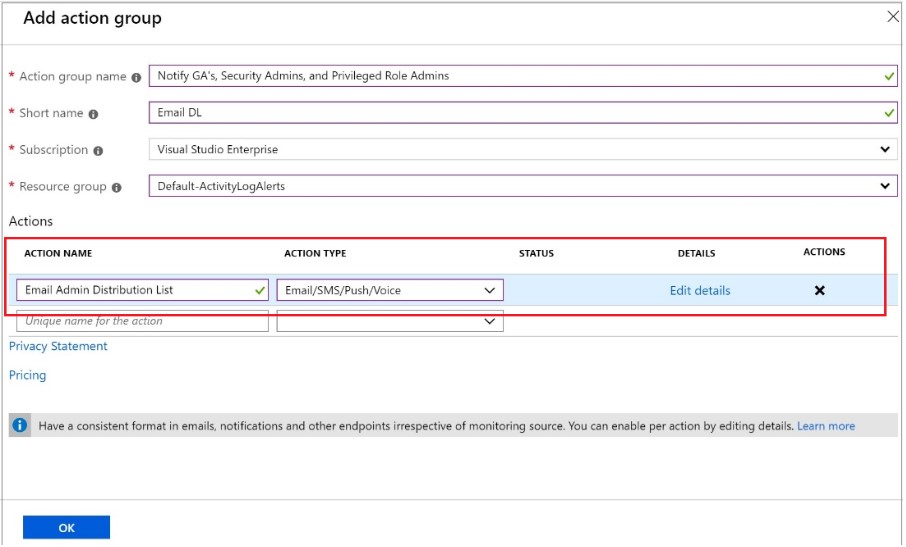
After entering that information, the crucial step is to assign the action to the group admins and pick the Action Type as Email/SMS/Push/Voice. After setting up this group, you will be notified regarding all break glass account activity every time an action is performed.
Final Word
Using a break glass solution is a great way to ensure your critical systems are accessible when you need them most. After reading this article, you will know what a break glass account is, when to use it, and how to set it up and utilize it properly.
Does Your Team Lack an Azure Skillset? Fortunately, Azure implementations are DCG’s expertise! With Microsoft-Certified experts, we can help you implement a break glass account for any situations that may arise. Contact us to learn more >>



