Develop | Secure | Maintain
Office 365 Security
Optimization Assessment
Your Office 365 environment is critical to your success as an organization. Learn how to develop, maintain and secure your Office 365 from cybersecurity risks and gain peace of mind that you have a strong security posture.
What is an SOA? (Security Optimization Assessment)
When it comes to cybersecurity risks and threat assessments, it’s important to understand the role that proactive education and assessments play in combatting downtime. It’s also crucial to develop a strong defense network to bolster your security posture. Our SOA aims to educate your team, develop a framework of industry-recognized functions to maintain protection, and detection posture that allows you to respond rapidly to the changes in cybersecurity threats. Read a list of our SOA controls below:
- Aligned with MITRE ATT&CK Framework
- Highly Automated with minimal manual collection
- Monthly New Controls and Updated Content
- Operational Survey
- Quality of Life, Updates, Budget Analysis, and Review
- Workloads Include: Identity, Devices, Email, Collaboration, and Processes
Engagement & Structure of SOA/SOAaS
SOA - Security Optimization Assessment
The SOA single-use assessment is a great tool for organizations looking to complete a cost-effective annual assessment of the Office 365 security structure and remediate any major security risks. This is great for small and medium deployments.
What is Included?
- Baseline Assessment (4 Days)
- Configuration Information Assessment
- Operational Survey
- Knowledge Transfer Sessions
- Final Remediation & Closeout Report
- Includes Data Comparison with a previous assessment
Time Frame:
The SOA is a comprehensive assessment that is completed over a series of workshops that span the course of four days. This includes onsite and off-site time. You can view the entire agenda below.
SOA as a Service
For some medium and large enterprise-scale deployments or organizations that have sensitive data and require more security and compliance, the SOA as a Service is the most cost-effective option with its annualized schedule and frequent checkpoints.
What is Included?
- Baseline Assessment (4 Days)
- Performance of the standard SOA
- Two Check Point Assessments (2 Days Each)
- Re-assessment of the environment to track remediation progress
- Final Assessment (3 Days)
- Performance of the final knowledge transfer and closeout
Time Frame:
The SOA as a Service is completed throughout the course of a year, during a 12 day time period. There are multiple planned checkpoints and assessments. You can view the entire agenda below.
Program Deliverables
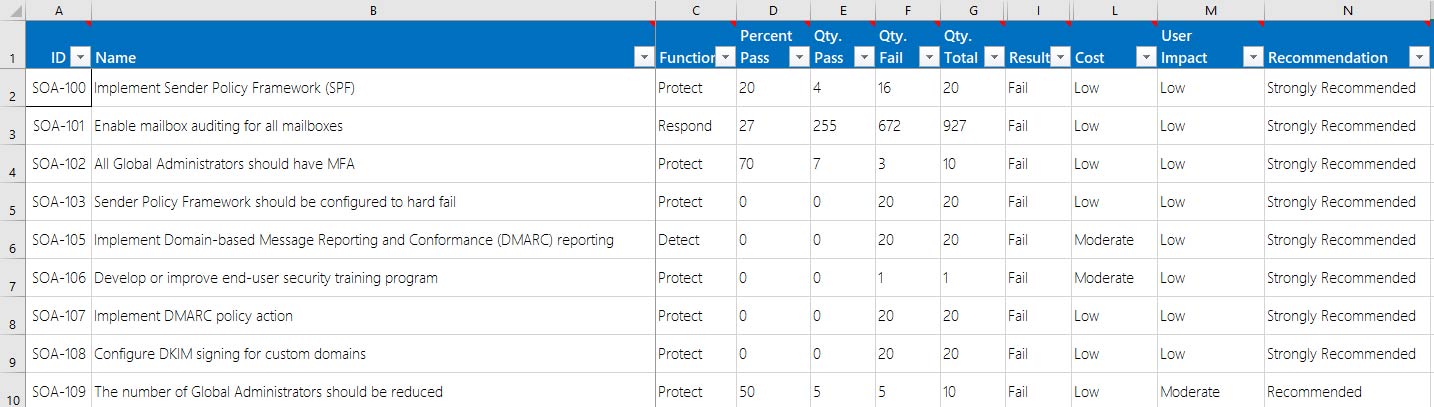
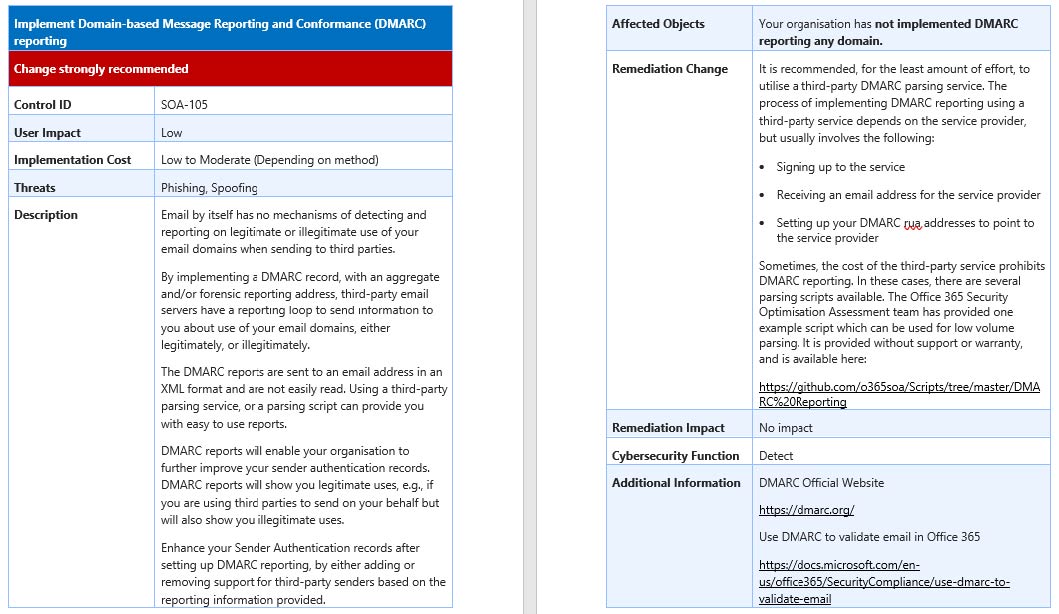
Remediation Planning Playbook
The remediation planning playbook is the overview document of all system controls with an overall indication of the user impact, cost, and urgency of the recommendation. This includes columns for customer urgency, owner, and due dates. This is included in the SOA as well as during each of the program checkpoints in the SOA as a Service. Click the image below to see a sample of the RPP document.
Knowledge Transfer and Closeout Deck
Workshops will be provided to you in a concise report once our team and Microsoft engineers collaborate to determine the action items, system controls, and the overall details from the email security, identity protection, security principles, and securing O365 services. A KT deck will be used over time during the next SOA engagement or SOA as a Service checkpoint.
SOA as a Service Deliverables
The SOA as a Service will include all of these deliverables plus continued security recommendations, trend reporting of remediation, and planning.
Office 365 SOA Engagement Structure Agenda
A Solution Health Assessment is a four-day proactive engagement, led by Dynamic Consultants Group, with your key stakeholders to review project objectives, processes, and technology, risks, and more. The result is a tailored solution assessment to assist you in achieving your project goals. Get a true view of your project and how our team can help you navigate the transition from project failure to project success.
| Workshop Day | Workhop Objectives | Internal Team Needed | Workshop Leader |
|---|---|---|---|
| Day 1 | Kick-off Meeting, Collection of Configuration Information and Operations Survey | IT Security, Office 365 Admin, & O365 Global Admin | Microsoft Engineer |
| Day 2 | Knowledge Transfer: Email Security and Protection | IT Security, Office 365 Admin, & O365 Global Admin | Microsoft Engineer |
| Day 3 | Knowledge Transfer: Identity Protection, Security Principles & Securing O365 Services | IT Security, Office 365 Admin, & O365 Global Admin | Microsoft Engineer |
| Day 4 | Closeout Presentation & Creation of Final Reports | IT Security and Senior Management | Microsoft Engineer |
Ready to Check your Office 365 Security?
SOAR: Security Optimization Assessment Remediation
Once a customer has completed the SOA, our team will help your organization remediating the findings. What good is an assessment if you have no way to actually fix the issues found? During this engagement, we focus on helping you to remediate the strongly recommended findings for Office 365. These are typically moderate or low-impact changes to your users but moves the needle fast to getting your security back in line. Take a look below to see what is in-scope and out.
In Scope
- Remediation of findings from the Security Optimization Assessment
- Additional Knowledge Transfer of the assessment finding
- Remediation Report
Out of Scope
- Troubleshooting of technical issues related to third-party applications
- High user-impact findings implementations
- On-Premise configuration changes
- Architecture or design review
SOAR Audience
The SOA and the SOAR engagements are targeted to bring value to the IT security team, including Security Architects, Support, and departmental business decision-makers. Their participation is critical to the successful outcome of this implementation. Additionally, participants should include Office 365 Global Administrators, Service Owners and Administrators as needed for changes, and Security Administrators. It is also strongly recommended that a Change Advisory Board (CAB) be represented during the programs.
SOAR Engagement Options
Discussion
This type of customer wants to discuss and target controls next up for remediation between touchpoints. They may drive which controls they want to target or rely on the customer engineer to manage the project. Typically, the first touchpoint will identify which controls will be targeted for a deeper discussion during a subsequent touchpoint.
Decision
This type of customer wants to see a demonstration of certain controls targeted for remediation between touchpoints. They may ask for validation methods to see the effects of previous control changes. Typically, the first touchpoint will identify which controls will be targeted for demonstration during a subsequent touchpoint.
Deployment
This type of customer wants to perform the remediation of controls during touchpoints. They may use pre-approved change management requests to drive which controls to remediate. Typically, the first touchpoint will identify which controls will be targeted for remediation (deployment) during a subsequent touchpoint.
SOAR Structure
The SOAR engagement spans five days and can be spread across multiple weeks for five days total (over a max of 30 days) including the kick-off, remediation, and validation.
Day One
Kick-off
Review the remediation planning playbook as a team to map out any planned changes and identify pilot users.
Day 2 - 4
Implementation
Implementation of the remediation items while working through the identified findings for pilot users.
Day 5
Validation
Review the implemented changes and plan a rollout to the rest of the organization based on the pilot users.
Outcomes should address remediation challenges through deployment walkthroughs, improve security posture, create process templates, and end with a management level closeout presentation.